Netflix and other US-based streaming sites like Hulu aren’t currently available in several countries. As a semi-legit workaround, many blocked countries are resulting to using VPN services or DNS redirection services to get around geoblocks.
I personally prefer the DNS services over VPN due to the simplicity of the bypass. However, while the DNS settings can be applied at the router level (and automatically apply to all devices), it does mean that all traffic requests are resolved through the remote server. To avoid this, several rules can be put in place on an OpenWRT enabled router to redirect only requests for certain hosts — specifically the ones we are interested in bypassing the geoblock.
These same rules can be used for other geo-DNS services other than Unblock-Us, simply substitute the required DNS addresses.
Host-Specific Rules for Unblock-Us on OpenWRT
/etc/config/ddns
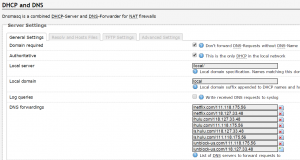
(or through the GUI, Network > DHCP and DNS > Sever Settings > General Settings)
config dnsmasq
list server '/netflix.com/111.118.175.56'
list server '/netflix.com/118.127.33.48'
list server '/hulu.com/118.127.33.48'
list server '/hulu.com/111.118.175.56'
list server '/s.hulu.com/118.127.33.48'
list server '/s.hulu.com/111.118.175.56'
list server '/unblock-us.com/111.118.175.56'
list server '/unblock-us.com/118.127.33.48'
Chromecast-specific rules
The Chromecast doesn’t currently allow users to specify custom DNS settings. They’re fixed to the Google DNS service, but we can utilise custom Firewall rules on OpenWRT to redirect the requests to specific DNS requests. This doesn’t achieve the per-host redirection, but at least limits it to the Chromecast’s traffic.
/etc/firewall.user
(or through the GUI, Network > Firewall > Custom Rules)
iptables -t nat -I PREROUTING 1 -d 8.8.8.8 -j DNAT --to-destination 111.118.175.56
iptables -t nat -I PREROUTING 2 -d 8.8.4.4 -j DNAT --to-destination 118.127.33.48

4 Responses
Hi Jake
Thanks for publishing this.
If I want our general internet DNS queries to go through OpenDNS, but the Chromecast to use a Smart DNS service, can I set the default DNS to the OpenDNS servers and then use the two iptable commands above to the DNS server of my Smart DNS provider?
Also, how would we find out the ip address or URL that Netflix , Hulu or Vudu uses for an Android app? (i.e. for the smart phone and tablet to control the Chromecast apps)
Regards
Dwayne
Hi Dwayne,
You should be able to set the OpenDNS DNS servers at the WAN connection level, which means all other request will be resolved using OpenDNS.
I’m no iptables expert but I imagine you could add the request IP in that mapping so that explicitly only Chromecast traffic (E.g. 192.168.1.50) goes to the Unblock-US servers — though the dynamic IP might also change.
I believe the Netflix app has hardcoded Google DNS as their resolver, so doing the above would break that.
Ultimately I think we’d need to use something like BIND on the router to masquerade as 8.8.8.8 then redirect based on the hostname.
Regards,
Jake
FWIW, the following entries in /etc/config/firewall seem to work to redirect the Chromecast to unblock.us. I like that a bit better than the raw iptables call.
config redirect
option src ‘lan’
option src_dport ’53’
option src_dip ‘8.8.8.8’
option dest_port ’53’
option family ‘udp’
option dest_ip ‘208.122.23.22’
option src_ip ‘192.168.1.50’
option dest ‘lan’
config redirect
option src ‘lan’
option src_dport ’53’
option src_dip ‘8.8.4.4’
option dest_port ’53’
option family ‘udp’
option dest_ip ‘208.122.23.23’
option src_ip ‘192.168.1.50’
option dest ‘lan’
Re my last comment, the directives below each ‘config redirect’ line must be indented. Or just use UCI to set them.